Validation Evidence
Real artifacts from device validation work. All data is redacted and anonymized.
These examples represent both identified vulnerabilities and verification of implemented controls.
Bluetooth Low Energy Traffic Capture
Wireless traffic was captured during normal device operation to verify whether communication was protected at the packet level.
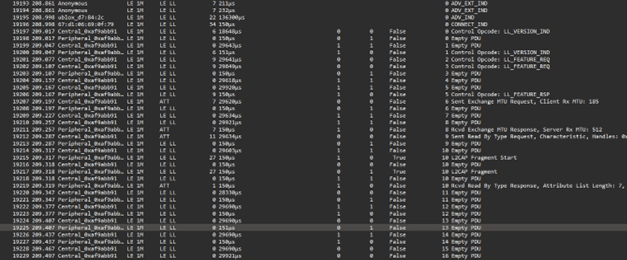
Overall BLE capture showing advertising, connection establishment, and attribute access during normal operation.
Finding: Unencrypted Bluetooth Traffic
Packet inspection revealed readable payloads prior to any authenticated pairing. Device identifiers and attribute data were observable in plaintext.
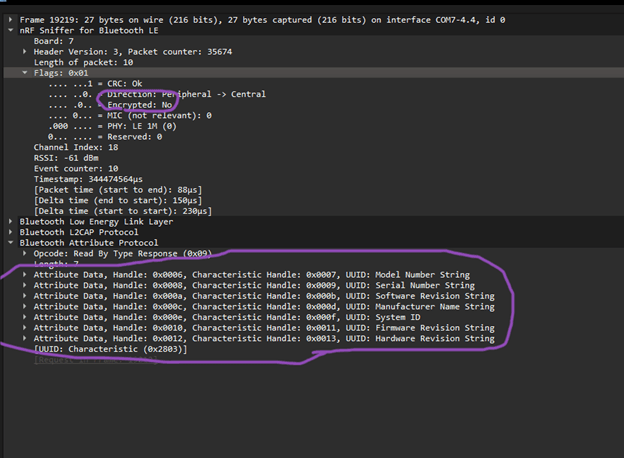
Specific BLE packet showing unencrypted payload data and exposed device attributes.
Impact: Unencrypted wireless traffic exposes device identity, operational data, or control interfaces to nearby observers.
Compliance: Secure communication required under ETSI EN 303 645, EU RED, and NIST IR 8259.
Solution: Encrypted Bluetooth Communication
Following implementation of authenticated pairing and encryption, packet captures confirmed that payloads are no longer readable.
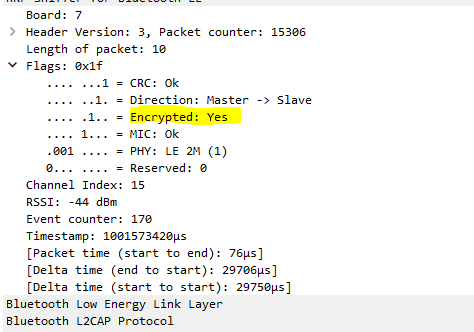
BLE packet capture after encryption implementation, showing protected payload data.
Controls addressed: Data in transit protection, authenticated pairing, confidentiality of device identifiers and operational data.
Network Exposure Assessment
Network interfaces were enumerated to identify exposed services and access paths. Testing was performed in an isolated environment.
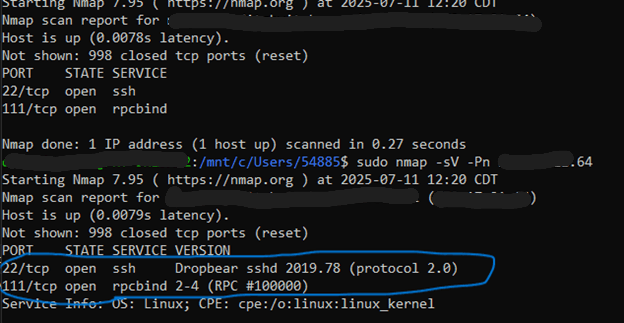
Port scan results showing listening services and accessible network interfaces.
Controlled Access & Exploitation Testing
Where exposed services were identified, controlled access attempts validated authentication strength and monitoring behavior.
Credential brute-force testing to evaluate access controls.
Reverse shell in emulated environment to validate detection and response.
Embedded Linux & Build System Validation
Build system reviewed to understand how security controls, logging, and monitoring could be introduced or validated.
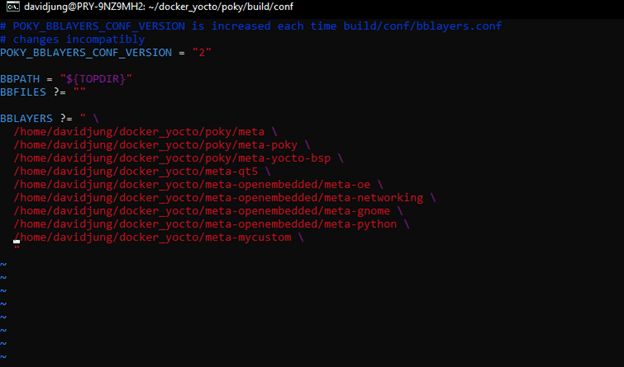
Custom Yocto layer for security functionality and validation hooks.
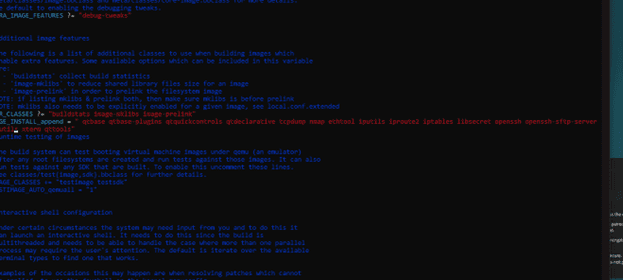
Build flags affecting runtime behavior and security posture.
Network Monitoring & Logging Validation
Initially, the device had no active monitoring. After implementing custom Yocto layers and tcpdump, network traffic could be captured and analyzed.
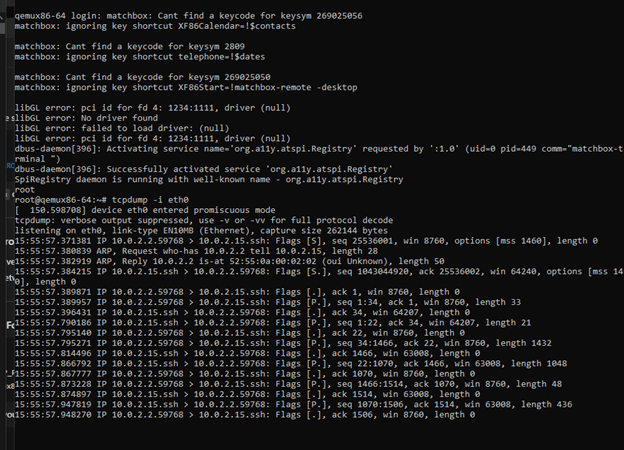
Network activity captured after implementing logging, illustrating visibility of device behavior.
Impact: Effective monitoring allows detection of unauthorized access attempts and provides forensic evidence.
Compliance: Logging and monitoring emphasized in IEC 62443 and NIST IoT guidance.
Database Security & Access Control
Backend database infrastructure configured with role-based access controls, encryption, and security policies to protect stored device data and user information.
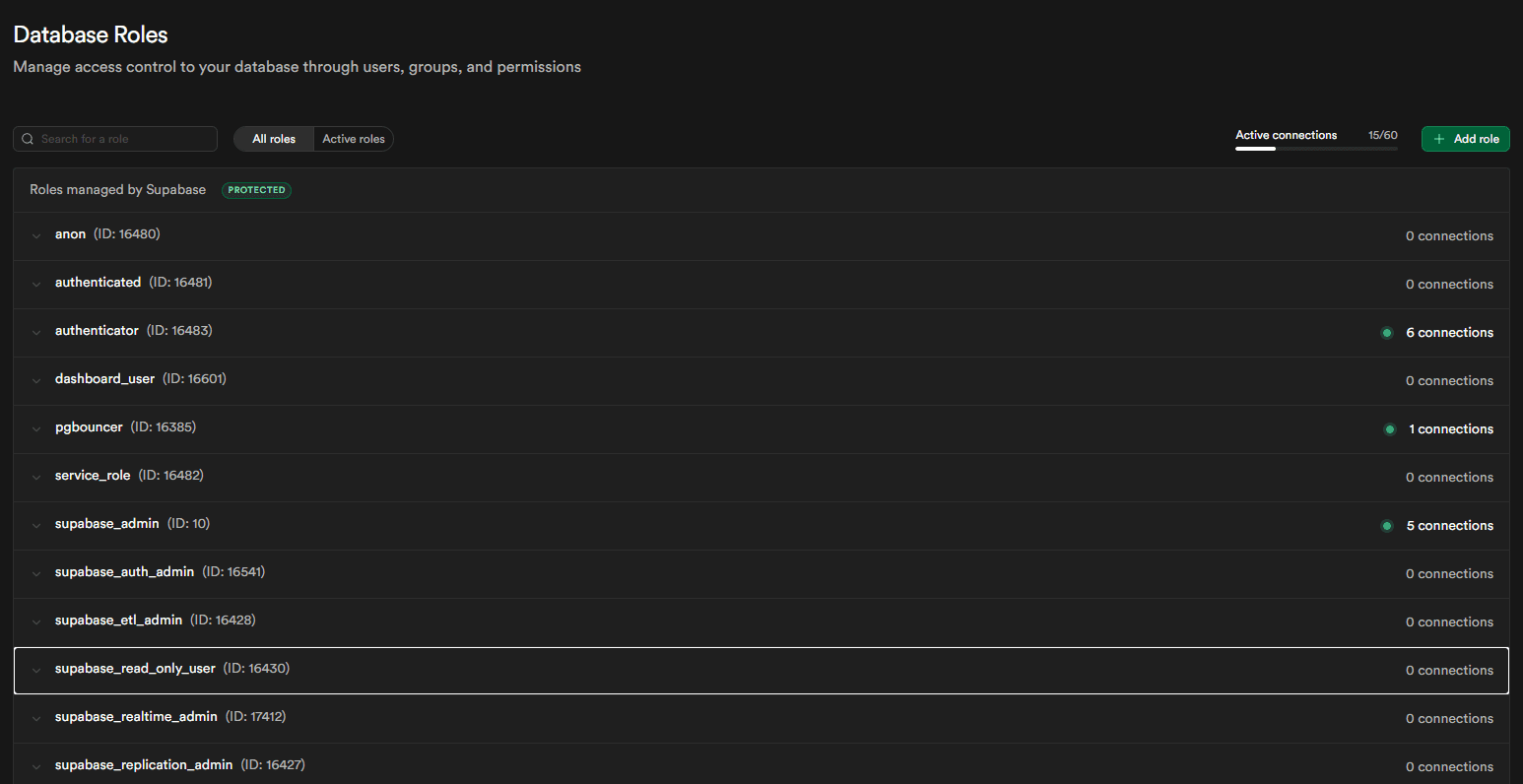
Supabase database showing Row Level Security (RLS) policies and access controls.
Security controls addressed:
- • Data at rest: Database encryption protects stored information
- • Access control: Row Level Security ensures users access only their own data
- • Authentication: Role-based permissions prevent unauthorized operations
- • Data integrity: Security policies enforce validation and prevent tampering
- • Audit capability: Access logging enables tracking of database operations
Compliance: Aligns with GDPR data protection, NIST 800-53 access control, and IEC 62443 zone isolation.
What These Examples Demonstrate
- • Verification of wireless encryption through packet-level inspection
- • Identification of exposed network services and access paths
- • Controlled exploitation to validate authentication and detection
- • Implementation and validation of monitoring after build system adjustments
- • Database security controls including encryption, access control, and audit logging
- • Alignment of findings with IoT security compliance expectations
These examples are representative and do not constitute certification or approval. They demonstrate independent technical validation of device behavior.